security policies : In this assignment, you will develop... | Computer Science
In this assignment, you will develop corporate policies for system security monitoring, patch management, and updates that cover both wired and wireless compone
From Assignment Stress to Stress-Free Grades. Trust your assignments to a professional online essay writer with the fastest delivery time and pure, original assignment papers.
Write My Assignment for Me.In this assignment, you will develop corporate policies for system security monitoring, patch management, and updates that cover both wired and wireless components. A web search will provide multiple examples of policy documents. The following resources may also be helpful as you draft your policy documents: SANS. No date. https://www.sans.org/blog/cis-controls-v8/?msc=main-nav . https://www.sans.org/critical-security-controls/?msc=main-nav This resource provides a list of case studies highlighting how security professionals have made improvements in their security controls. SANS. No date. Security Policy TemplatesLinks to an external site.. https://www.sans.org/information-security-policy/ This resource provides a number of security policy templates that might be helpful in drafting your policy documents. The specific course learning outcome associated with this assignment is: Recommend best practices for monitoring, updating, and patching systems. Instructions Write a paper in which you: Establish a system security monitoring policy addressing the need for monitoring, policy scope, and exceptions and supported by specific, credible sources. Justify the need for monitoring. Define the scope of the policy (the personnel, equipment, and processes to which the policy applies). Provide guidelines for policy exceptions, if approved by the IT and Security departments. Establish a system security patch management and updates policy addressing the need for patch management and updates, policy scope, and exceptions and supported by specific, credible sources. Justify the need for patch management and updates, aligned with ISO/IEC 27002. Define the scope of the policy (the personnel, equipment, and processes to which the policy applies). Provide guidelines for policy exceptions, if approved by the IT and Security departments. Support your main points, assertions, arguments, or conclusions with at least four specific and credible academic sources synthesized into a coherent analysis of the evidence. Cite each source listed on your source page at least one time within your assignment. Order this assignment or a similar task.
Why Students Trust Us for Top Grades
Zero-Plagiarism Papers - Original writing by experts with free turnitin reports on-demand.
We Protect Your Privacy - Anonymity and Security with zero-data-sharing policy.
Free unlimited edits - We revise your paper until you are satisfied free of charge.
24|7 Support - We are available to answer your question every second of the day.
Best Writer - We connect you to the most suitable expert writer for your requirements.
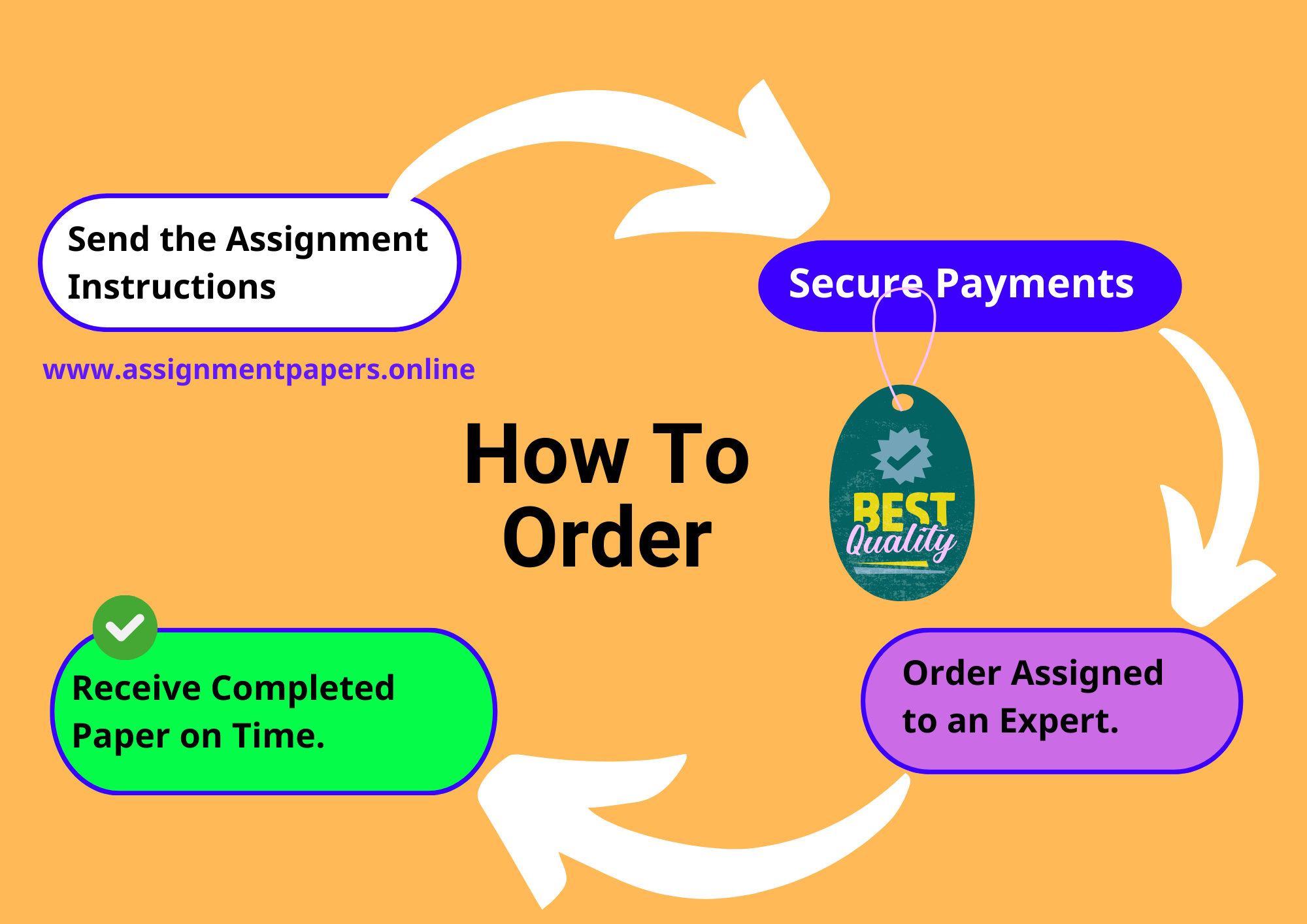
How to order: Working with A Top Assignment Writer Online
What You get: With 100% Money-Back Guarantee
Unlimited Revisions Free
Title Page and References Free
Formatting Free
Outline Free
Best Writer Guaranteed
Plagiarism Report Guaranteed
Make your Studies stress-free and effort-free with our online essay service.
Write My Paper RegisterClaim 30% OFF on first Order.
All Solutions are 100% original protected with Zero-Plagiarism Policy.
Recent Assignment Tasks/Orders
CWUD Case Project: Develop a Survey
Create a short multiple choice survey of 25 questions or less to determine an ACME employee’s level of knowledge regarding security awareness. The survey sho
Computer Science
ViewGrCA march 1 2025: Topic: The Negative Effects of Social... | Computer Science
Topic: The Negative Effects of Social Media on Teenage Mental Health
Computer Science
View